Secure IT

Secure IT
Future-ready Cybersecurity Services
With so much to keep track of, businesses want comprehensive protection that is both easy to manage and intelligent enough to fend off growing threats. As you navigate and manage this complex environment, our IT security services provide you with a piece of mind. We’ll work with you to create, execute, and optimize a tailored, comprehensive, compliance, and future-ready cybersecurity plan.
Understanding where and how your IT system is sensitive to hazards is the first step in securing your people, devices, and data. Next, we uncover your most critical remediation needs through compliance audits, penetration testing, and focused assessments. Once we’ve thoroughly understood your current status, we also work with you to establish a roadmap that tackles your existing gaps, compliance and regulatory requirements, and business goals.

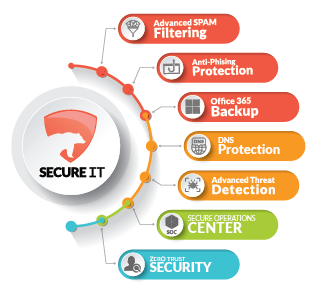
Advanced Spam Filtering
- Advanced antivirus protection
- Behavior analysis instead of signature detection
- Machine learning threat analysis of applications
- Roll-back capability

System Failure
- Cloud-based protection using sandboxing and malicious link databases
- AI-based anti-phishing determination tool
- Mailbox-level anomaly detection
- Collective phishing campaign detection
- Direct integration with Microsoft Outlook and Outlook Mobile
- Alternatively, concerns may be forwarded to a phishing reporting email address

Office 365 Backup
- Backup beyond Microsoft O365, including email (Exchange Online), OneDrive, SharePoint, Teams, Groups, Calendars, Tasks, and Attachments
- Increased control over the retention period
- Easier to use and restore from than built-in O365 recovery tools
- Meets compliance for HIPAA, GDPR, SOC, etc.

DNS Protection
- Automatic protection from malicious websites and servers
- Protects against more than just web-browsing attacks
- Works BEFORE the communication request is processed
- One of the fastest DNS response times in the industry

Advanced Threat Protections
- Continuous dark web scans for stolen credentials (emails, usernames, passwords)
- Stolen credentials notifications
- Automatic alerts to ABMTG Support
- Scans up to 3 domains for each Secure|IT client

Secure Operations Center (SOC)
- Stop Breaches and say ahead of your cyber adversaries.
- We are using Managed Detection and Response analysis to detect what others miss.
- Combines network visualizations, trade craft detection, and endpoint security to detect and neutralize lateral movement in the early stages rapidly.

Zero-trust Security
- Empower your users to work more securely anywhere and anytime, on any device.
- Enable digital transformation with intelligent security for today’s complex environment.
- Close security gaps and minimize the risk of lateral movement.

Cybersecurity services for your cloud adoption journey
The cloud has altered the way you do business – and how you secure your IT infrastructure. We’ll work with you to develop a tailored plan that develops with your organization as you modernize your IT and move away from traditional security platforms.
Secure IT – Protecting Your Business
Background
Small and Medium-sized businesses make up 44% of the U.S. economy. Cyber security should be a part of the strategy, whether a company plans to use cloud computing or email and maintain a website. The theft of digital information has surpassed physical theft as the most commonly reported fraud. Every company that uses the Internet is accountable for developing a security culture to boost consumer and business confidence.
Challenge
IT security measures can be costly, and many SMBs believe they won’t fall victim to attacks. Those businesses that take precautions often think that one product is enough or that their business is safe because they are in the cloud. Unfortunately, this is not the case. Attacks are becoming more advanced, cloud ransomware is real, and a single system alone cannot prevent all threats. Also, ransomware costs are high, and your business could be liable to pay penalties for breaches. Cloud service providers retain data for up-to30 days, and retrieving stolen data is challenging.
Solution
ABM Technology Group’s cyber security experts use the best tools and products on the market, developing a multilayered approach to protecting your business from cyber threats. Our product is called Secure IT, an information security program designed to protect your business against threats from every angle. In addition, our experts are proactive, stopping threats before they happen. We analyze web content, scan emails, and protect your data using advanced filtering, machine learning, and artificial intelligence.
Outcome
Take the guesswork out of cyber security with Secure IT powered by ABM Technology Group. Increase your network protection. Prevent phishing attacks. Interrupt information theft and protect your business by monitoring the dark web for data breaches. Save time, money and your data with a single solution — Secure IT powered by ABMTG.
Download the flyer
Enhance your cyber security with Secure IT from ABM Technology Group. Improve your network’s defenses, stop phishing attacks, and prevent information theft by keeping an eye on the dark web for data breaches. Choose Secure IT from ABM Technology Group for a straightforward solution that protects your time, money, and data.
Want to talk with an expert?
Our IT experts are here to help with all your needs.
They can answer all your IT-related questions from
the Microsoft pricing changes to Cybersecurity.
Or visit our page – Schedule a call
